


The growing interconnection of machines and connected objects to companies' information systems requires a complete overhaul of organizational structures to protect against external threats, internal threats, and insecure connected objects.
THE AUDIT CONSISTS OF THREE PHASES




01
Identifying vulnerabilities in your systems
Evaluation
02
Assessing the criticality of risks, their impact on the company, combined with their probability of occurrence
Action Plan
03
Developing a Quality Assurance and Security Plan to enhance the company's security level
Vulnerability Scanning
.webp)







Simulating real-world cyber attacks
Compliance with standards (PASSI, ISO27001)
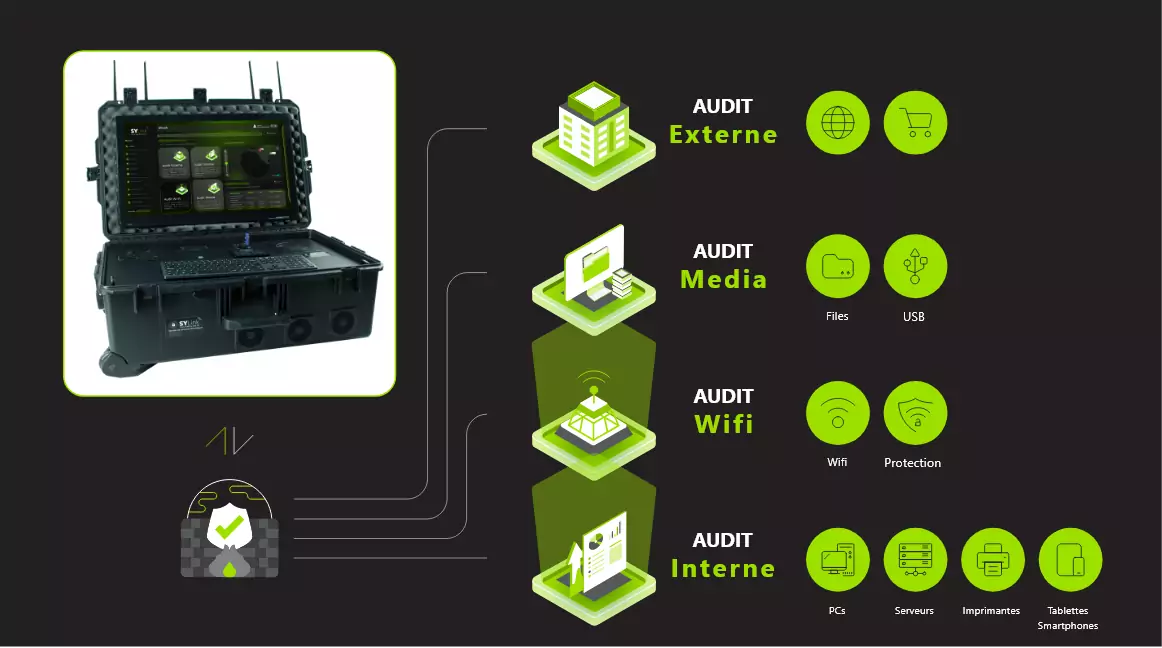
4 Types of Audits
• External Audit • Internal Audit • WiFi Audit • Media Audit
External Audit
An audit that provides visibility into the services and resources exposed to the internet, assessing the attack surface and the risks that could impact the Information System.
Internal Audit
This audit allows identification of all vulnerabilities in a company's network infrastructure. It scans all shared services in the network, such as FTP, SSH, etc.
WiFi Audit
The WiFi audit scans the WiFi networks accessible from your company and checks their security configuration, allowing identification of WiFi networks that pose a threat.
Media Audit
An audit that scans all devices, such as USB drives, hard drives, etc. Devices that pose a threat will be highlighted. It includes brute-forcing encrypted files' passwords and automatic search for sensitive data.
Audit Report
A concise report that allows for a quick understanding of the situation. The report does not require technical expertise to read and comprehend.
Action Plan Development
Development of a Quality Assurance and Security Plan to enhance your company's security level





Risk Assessment (CVE)
Active Directory Audit
Office 365 Audit
Website Audit
WiFi Audit and Security
File Audit (Malware / Personal Data)
Phishing Campaign
Access Control (web, ftp, ssh, etc.)
Firewall Monitoring and Verification
Account Leak Audit
GDPR Audit
Reinforced Case
27-inch Touch Screen
CPU: AMD Threadripper 3970x (64 threads) at 4.5 GHz
GPU: Nvidia RTX 3090 - 24 GB
1 ALFA AWUS WiFi + 1 WiFi card
4G Modem Router + 80 GB/month SIM card
Real-Time GPS LoRa Tracking Module (3 months autonomy)
RAM: 128 GB DDR4
Storage: 2 TB (2 x 1 TB Raid 0) nvme Gen4 (7000 MB/s)
12-key StreamDeck
2 RJ45 10 Gb Ethernet
Ventilation System with Control
Biometric Lock
sylink.fr
+33 (0)4 15 54 00 00
+33 (0)7 87 35 94 69